Continuing from our previous discussion, "Essential Security Measures to Safeguard Against Threats in IoT Devices", let's take a deeper look into the essential security measures for IoT devices. Last time, we discussed global security requirements set by each country, highlighting the Root of Trust, protection of highly confidential security parameters and personal data, and lifecycle management. I also introduced how Renesas achieves this Root of Trust through RX MCUs with integrated Trusted Secure IP (TSIP) and a comprehensive software package.
But now, a pressing question: How should we approach the protection of highly confidential security parameters and personal data?
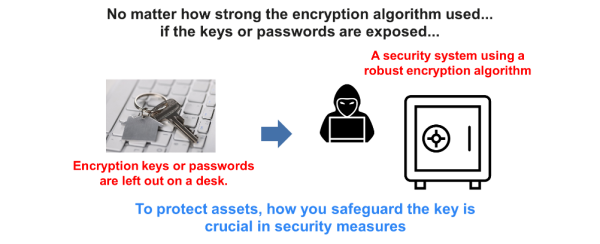
It's just like our daily routines: When we leave home, we lock the door and take care not to lose the key. Similarly, in the realm of cybersecurity, safeguarding cryptographic keys is paramount. No matter how robust your data protection system is, it's rendered ineffective if keys or passwords are carelessly exposed.
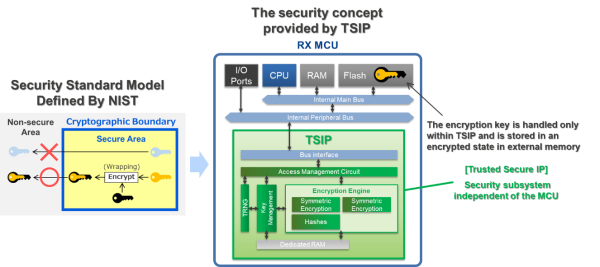
Renesas has focused on the standards set by the National Institute of Standards and Technology (NIST), leading to the implementation of a subsystem (TSIP: Trusted Secure IP) separated by cryptographic boundary within the MCU. This ensures that cryptographic keys are dealt with solely within the TSIP and always stored in external memory in an encrypted form, offering a 'Secure Key Storage' feature.
Let's dive into how the Secure Key Storage mechanism protects the key data.
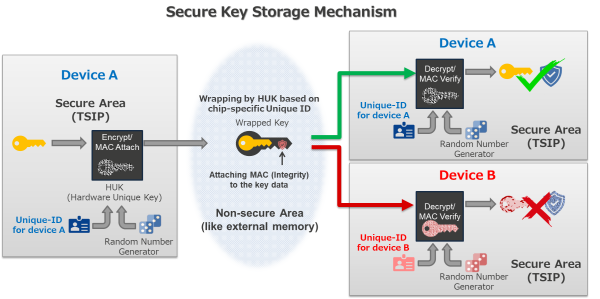
The TSIP generates the Hardware Unique Key (HUK) within a secure area (inside the TSIP) from each device-specific Unique ID and Random Number Generator. The HUK is used to wrap the user's key data, and the system always outputs it in a format known as the "Wrapped Key" to a non-secure area. Since the HUK is generated within TSIP based on the unchangeable, device-specific Unique ID and Random Number Generator, it is never exposed to the outside. Given the Unique ID is different for other MCUs, even if the key data is replicated, it can't be decrypted. Moreover, a Message Authenticate Code (MAC) is also attached to the Wrapped Key, making it possible to detect key data corruption during decryption.
Thus, TSIP isn't just a mere cryptographic accelerator. With it, the key data, in the unreadable "Wrapped Key" format, can be stored anywhere - be it code flash, data flash, or external memory. Since replicas can't be created, the confidentiality and integrity of the key information are ensured. Protecting key information directly translates to safeguarding confidential security parameters and personal data.
At Renesas, we currently offer RX microcontrollers equipped with two types of security engines: TSIP and TSIP-Lite. While TSIP and TSIP-Lite differ in the cryptographic suites they feature, both have the Secure Key Storage mechanism mentioned above, providing robust protection for key data.
On the other hand, we explained that TSIP does not allow plain key input from non-secure areas, and the wrapped key is never exposed externally because the HUK is generated within TSIP. So, how should the user's initial key data be wrapped and input?
While we omitted this in the main explanation, TSIP is equipped with a secure key provisioning mechanism related to lifecycle management, addressing this issue. We'll discuss this in the next session.
For an overview of the RX TSIP Security Solution, visit our RX Security Solutions page.